Pre-receive hooks that verify the Git commit message, the modified files and implement similar code change controls used to be requirements of large enterprises working in regulated industries only.
That seems to be changing.
Maintaining a clean and consistent repository with precise commit history is becoming a standard among software teams of all types and all sizes. Development team leads are actively looking to introduce commit best practices and source code management standards. These team leads recognized that standards improve code and product quality, speed up the release process, and strengthen the security of Git repositories.
Using Jira and Bitbucket Cloud for development?
Advanced commit verification with Jira work item checks and pull request rules are just as crucial in Bitbucket Cloud as on Data Center to ensure code quality, compliance, and traceability.
✅ Install Better Commit Policy Connector for Bitbucket Cloud
📖 Learn more about enforcing commit rules in Bitbucket Cloud
They also don't script their commit hooks from scratch and maintain those themselves. They turn to the Atlassian Marketplace, where they can select from supported, purpose-built commit verification apps.
There is a selection of top-rated, advanced commit verification apps that offer much more than just checking if a commit is linked to a valid Jira issue. These apps are made by developers for developers, covering the exact needs and requirements of this picky bunch.
Commit policy apps for Bitbucket
Bitbucket Data Center
This isn't an app, but it's fair to start with the incumbent to establish a baseline. Note that apps have to offer more than what's built-in to Bitbucket, otherwise, there is no point in investing in an app. At the same time, the commit policy app category can thrive partly because Bitbucket itself does not offer a lot of sophisticated pre-receive hooks.
According to the Bitbucket documentation, it comes with built-in pre-receive hooks to:
- Reject Force Push
- Verify Commit Signature (rejects commits and tags without a verified GPG signature)
- Verify the Committer
These are handy, but most of the complex commit verification requirements of software teams would be impossible to implement with just these.
Default pre-receive hooks work on the Bitbucket server-side, so commit verifications and rejections happen when developers are pushing their changes to the server. No local verification is offered, which means in case of many rejected commits it's would be time-consuming and painful to find and fix the non-compliant commits. The above Bitbucket pre-receive hooks don't offer much customization, either.
Want to hear more on local commit verification? Keep on reading!
Control Freak Hook for Bitbucket
Control Freak Hook offers a wide range of policies from the formal verification of your commits and its authors to the more complex use cases, like prohibiting foxtrot merges. In contrast to Bitbucket's pre-receive hooks, it would not fit this blog to list all the features, so let's just highlight some key capabilities.
You can set up rules to ensure committers are valid Bitbucket users, or be stricter and require them to be the currently-logged-in user who performs the push. You can define tag or branch management policies to check naming conventions and prevent unwanted tag creation or deletion.
Some Control Freak Hook features exist to boost existing Bitbucket features, like the Approval Policy, which is similar to Bitbucket's minimum approvals or default reviewers controls. The app does more than Bitbucket by allowing these checks globally, and by adding many additional options like ignoring self-approvals or approvals from read-only users (Note that these features require the PR-booster app).
Control Freak Hook checks commits at push time, no signs of local commit verification options.
Control Freak Hook features can be customized to fit the developer team's need, however, the rejection messages can't be personalized.
Better Commit Policy for Bitbucket
Better Commit Policy for Bitbucket was one of the first products that came out to answer the software developer managers' growing need for code change verification.
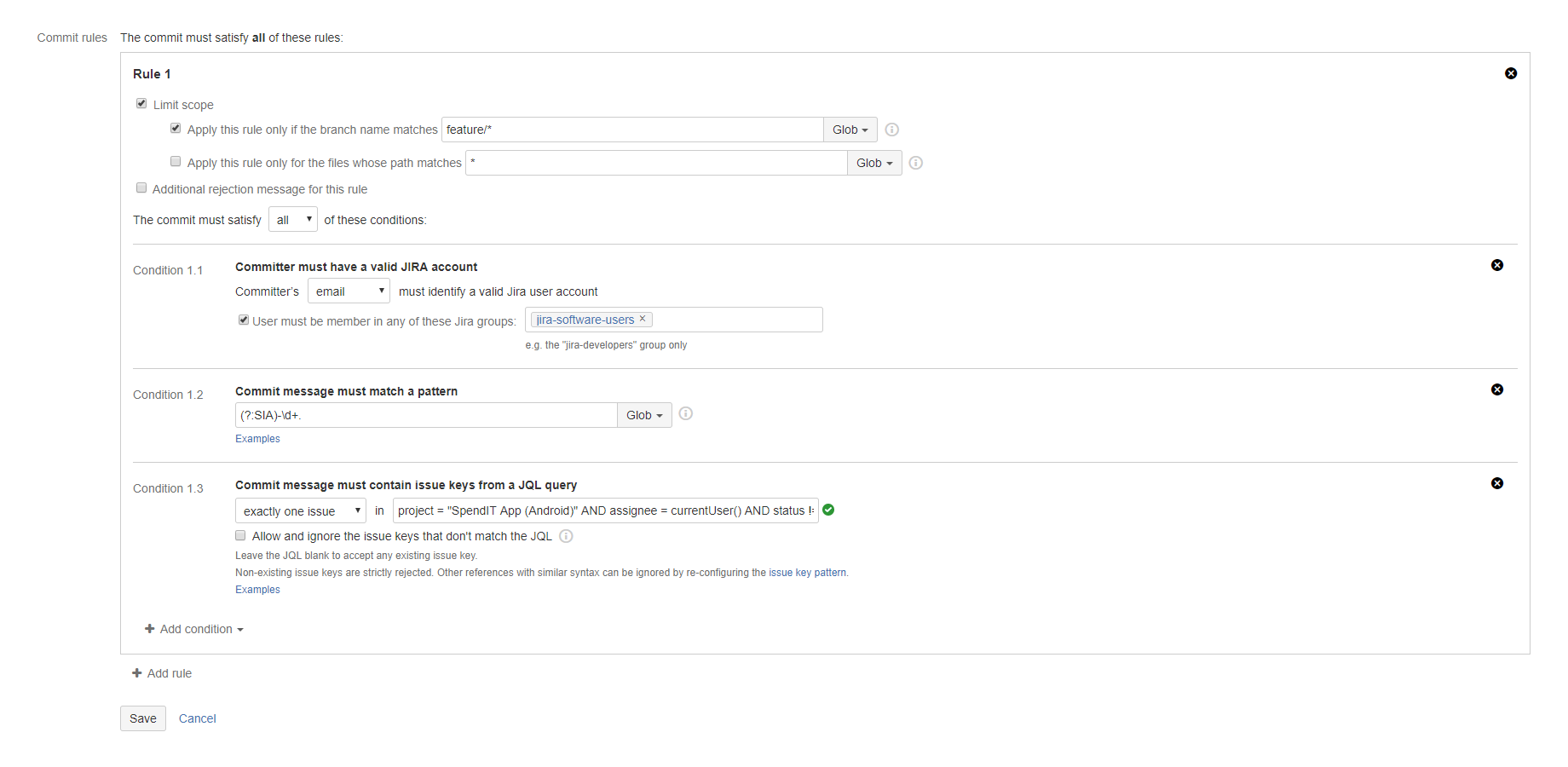
Similar to Control Freak Hook, it offers many options to set up your commit check strategy. It relies on a Jira counterpart app that does the heavy lifting and that's where you can manage your policies as well.
Commit policies can check for the usual things like the committer user's validity or their email address format. You can turn on controls for file path and file format to protect certain directories or require (or reject) certain file types.
Your branches and tags can have their own rules as well, requiring them to include Jira issue keys, test IDs, or follow a naming convention.
Commit messages can also be verified for length and content, so you can make sure they start with or contain a certain identifier, like a Jira issue key. You can enforce the 50/72 commit message rule or any message pattern that fits your workflow.
The rejection message is customizable, so instead of throwing an ugly Regex into your developers' faces, you can include easy-to-read instructions.
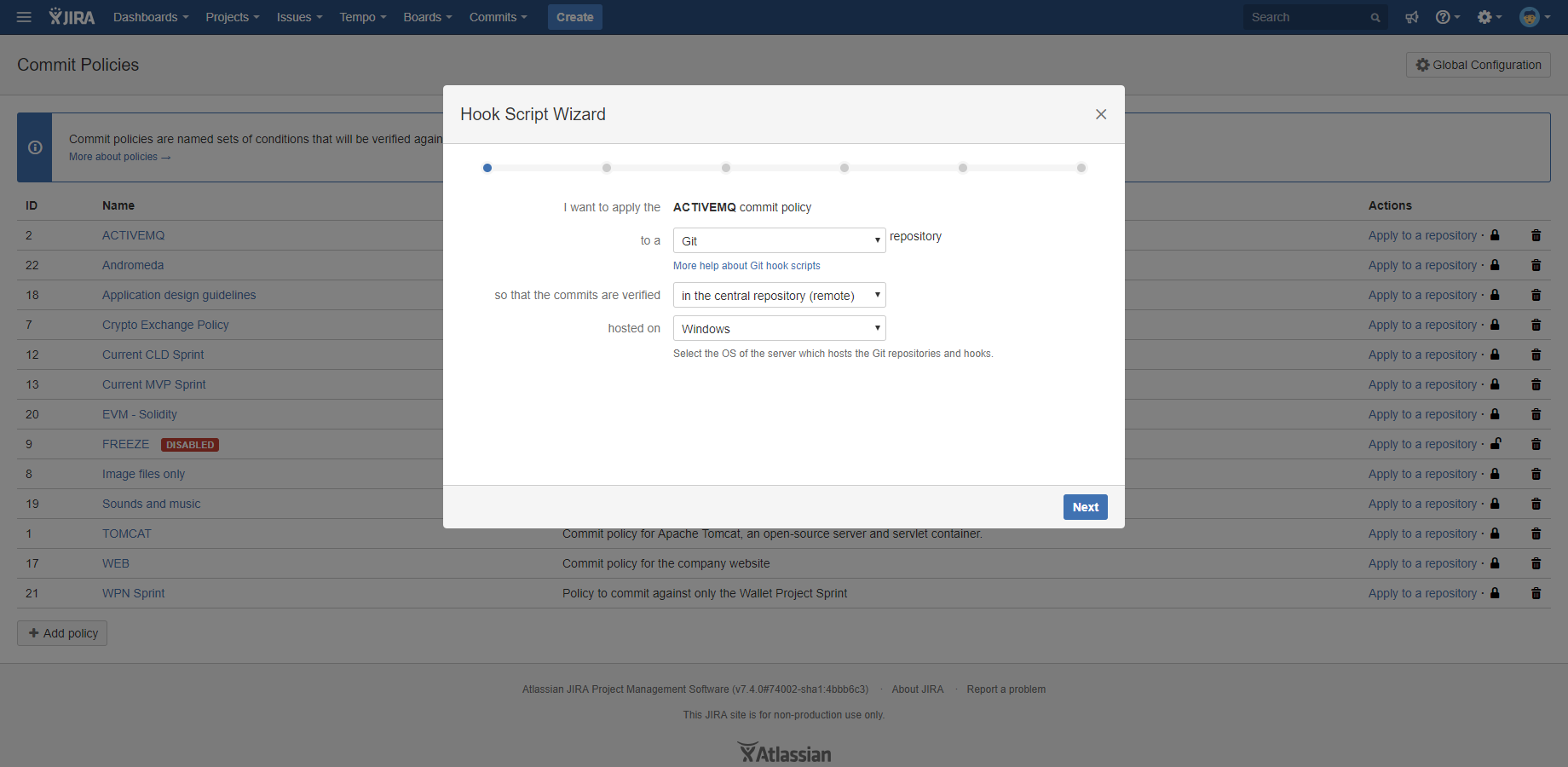
Local commit verification is Better Commit Policy's strength. Local, or client-side hooks prevent non-compliant commits at commit time before they are even made. This eliminates the efforts required to fix rejected commits at push time and makes your team faster and more productive.
Instead of instructing to create and configure a hook file by hand, Better Commit Policy provides a hook script wizard, that creates the pre-configured local hook scripts for you with a few clicks. You only need to copy and paste the files into your local Git repository and ready to go!
Jira Hooks for Bitbucket
As the name suggests, Jira Hooks for Bitbucket is focused mostly on Jira-related verifications. It can check several aspects of the pushed changes, including the Jira issue key in the commit message and branch name, and verify if the mentioned Jira issue is in the desired status. As you would expect, you can enforce a commit message pattern as well and ensure the right Jira issues are mentioned via JQL.
Jira Hooks for Bitbucket provide an option for local commit verification. Although, creating and installing the client-side hook script is more of a manual, more error-prone process, not automated. The app's documentation contains the instructions to follow for implementing local commit verification.
Yet Another Commit Checker
Yet Another Commit Checker started as a free app but changed owners in the past to become a professionally supported paid app for Bitbucket Server and Data Center.
It is capable of the basic commit verifications that you would expect. It can verify the committer's name and email, check for patterns in the commit message and enforce branch naming conventions.
Yet Another Commit Checker pre-receive hooks and merge checks are performed when changes are pushed and no local commit verification is offered for developers.
It's only available for Bitbucket Server and Data Center. If you are using Bitbucket Cloud, your best bet is to look into Better Commit Policy Connector for Bitbucket Cloud, which is the best YACC alternative for Bitbucket Cloud users.
ScriptRunner for Bitbucket
Chances are high that you already know ScriptRunner, as it is a household name in the Atlassian Ecosystem. It's not a commit verification app, but ScriptRunner for Bitbucket can be used to introduce repository checks and commit policies of your choice. The nature of ScriptRunner is that almost every feature can be implemented with it - if you are willing to code.
You don't necessarily have to code, since the Adaptavist Library contains pre-written scripts for some use cases. Keep in mind though that not every use case is covered. In contrast to the other apps, you are responsible for maintaining and supporting your custom commit verification scripts in ScriptRunner.
Evaluate a commit policy app today
The built-in pre-receive hooks in Bitbucket can get you started, but for advanced commit verification strategies you can turn to several Marketplace Partners. The teams behind these commit policy apps have been there, done that, and will find the right solution for your exact use case.